Affiliate de-cloaking : how to discover affiliate violations

Your affiliate compliance looks clean. Landing pages show affiliate disclosures. No competitor mentions. Everything looks perfect during your monthly review.
But there is one thing that can happen : those same pages show different content to real users.
When your compliance team visits, affiliates serve a "safe page" with compliant content.
When customers click through, they land on a "money page" with unauthorized claims, missing disclosures, or competitor promotions.
This is cloaking : and it's why classic affiliate monitoring misses this type of violations.
Affiliate decloaking is the process of revealing what affiliates show to users, versus what they show to compliance teams.
Without decloaking capabilities, you're only seeing what fraudulent affiliates want you to see.
What is affiliate cloaking (and why affiliates use it)
Cloaking means serving different content based on who's viewing a page.
The technique categorizes traffic, then make a decision :
- Is this a real user or a bot ?
- Is this IP from a brand's office?
- Is the referrer a verification service?
Based on these signals, cloaked pages redirect visitors to different destinations, or display different content.
Legitimate uses of link cloaking
Not all cloaking is malicious. Affiliates (sometimes) use basic link cloaking for valid reasons :
- URL simplification : Converting long affiliate URLs with tracking parameters into clean, branded links (using tools like pretty links, for exemple)
- Link management : Centralizing affiliate links, so updates only require changing one destination
- Analytics : Tracking click performance across campaigns and channels
- A/B testing : Testing different landing pages with the same promotional link
These practices are transparent. The final destination matches what users expect, and the content is consistent, regardless of who visits.
Malicious cloaking to hide violations
The problem starts when affiliates use cloaking to hide policy violations.
Specialized cloaking platforms like Adspect, JustCloakIt, and MagicChecker are specifically designed to evade brand monitoring.
These systems detect verification attempts using multiple signals:
- IP reputation databases : they identify IPs associated with brands, agencies, or monitoring services
- Browser fingerprinting : they detect headless browsers and automation tools
- Geographic filtering : they block traffic from locations near brand headquarters
- Referrer analysis : they identify traffic from known verification platforms
- Behavioral patterns : they flag visits that don't match normal user behavior
When the cloaking system detects a potential verifier, it serves the safe page.
When it identifies a real user, it serves the money page, which often contains the actual violations.
Types of cloaking techniques to detect
Decloaking requires testing multiple parameters.
Sophisticated affiliates often combine several techniques. Checking only one method can miss violations, hidden behind others.
User-agent cloaking
The most common technique.
Pages serve different content based on the browser, or bot identification string. An affiliate might show compliant content to Googlebot while showing unauthorized claims to Chrome users.
This extends to AI crawlers too.
With tools like GPTBot and ClaudeBot now crawling the web, some affiliates specifically target these user agents with different content.
What to test : Googlebot, Bingbot, mobile bots, AI crawlers (GPTBot, ClaudeBot), and standard browser user agents.
IP and geographic cloaking
Pages serve different content based on visitor location or IP type.
Affiliates targeting US customers might cloak their pages to show compliant content to European IPs (where many monitoring services operate), while serving violation content to American visitors.
Some cloaking services maintain databases of datacenter IPs, VPN exit nodes, and known verification service ranges.
What to test : Multiple countries, residential vs datacenter IPs, VPN detection.
Referrer cloaking
Content is changed based on where the visitor came from.
A page might show clean content when accessed directly (how most verifiers check), but show different content when the referrer is Google Search, Facebook, or other traffic sources.
This is relevant for PPC brand hijacking, where affiliates run ads that look like official brand ads but redirect through cloaked affiliate links.
What to test : Google Search, Bing Search, Facebook, Twitter/X, Reddit, direct access (no referrer).
JavaScript cloaking
Some pages render differently, depending on whether JavaScript executes.
Search engine crawlers historically didn't execute JavaScript well, so affiliates would hide violations in JS-rendered content that bots couldn't see.
Modern bots execute JavaScript, but the technique persists, especially targeting verification tools that might not render pages.
What to test : Compare content with JavaScript enabled vs disabled.
Device cloaking
Mobile and desktop users see different content.
An affiliate might maintain compliant desktop pages (which verification teams typically check) while serving violating mobile pages (where most real traffic converts).
What to test : Desktop vs mobile rendering, different screen sizes.
Cookie-based cloaking
First-time visitors see different content than return visitors.
Affiliates might show compliant content on initial page load, then serve different content once tracking cookies identify a return visit.
This makes spot-checking ineffective since verifiers rarely simulate return visits.
What to test : Fresh sessions vs sessions with existing cookies.
What affiliate decloaking reveals
When you successfully decloak affiliate pages, you often find violations that would otherwise go undetected for months.
Hidden trademark biddin : Affiliates running Google Ads on your brand terms while cloaking the landing pages, to hide their affiliate identity from your monitoring.
Removed FTC disclosures : Pages that show proper disclosure to verification traffic but remove it for real users. A compliance violation that exposes your brand to regulatory risk.
Competitor promotions : Affiliate pages that appear brand-focused to monitors, but actually promote competitors to real visitors, diluting your traffic and attribution.
Cookie stuffing scripts : JavaScript that only executes for real users, dropping affiliate cookies without genuine clicks.
Unauthorized claims : Product claims, pricing, or promotions that violate your affiliate agreement, but are hidden from compliance checks.
Redirect manipulation : Clean-looking pages that redirect real users through unauthorized tracking or to completely different destinations.
How to decloak affiliate links
Manual decloaking methods
Basic decloaking is possible without tools.
VPN testing : Access affiliate pages through VPNs in different countries. This catches geographic cloaking.
Browser manipulation : Test with different user agents using browser developer tools. Change the user agent to Googlebot, and compare what you see versus a standard Chrome user agent.
Incognito mode : Test with fresh browser sessions to detect cookie-based cloaking.
Clear all cookies and compare against logged sessions.
Mobile testing : Check pages on actual mobile devices (not just responsive previews). Some cloaking detects the difference.
The limitation of manual methods: sophisticated cloaking systems detect these attempts. They identify VPN IP ranges, recognize developer tool manipulation, and flag behaviors that don't match real users.
PageRadar cloaking checker
For systematic decloaking, PageRadar's free cloaking checker tests multiple detection methods simultaneously.
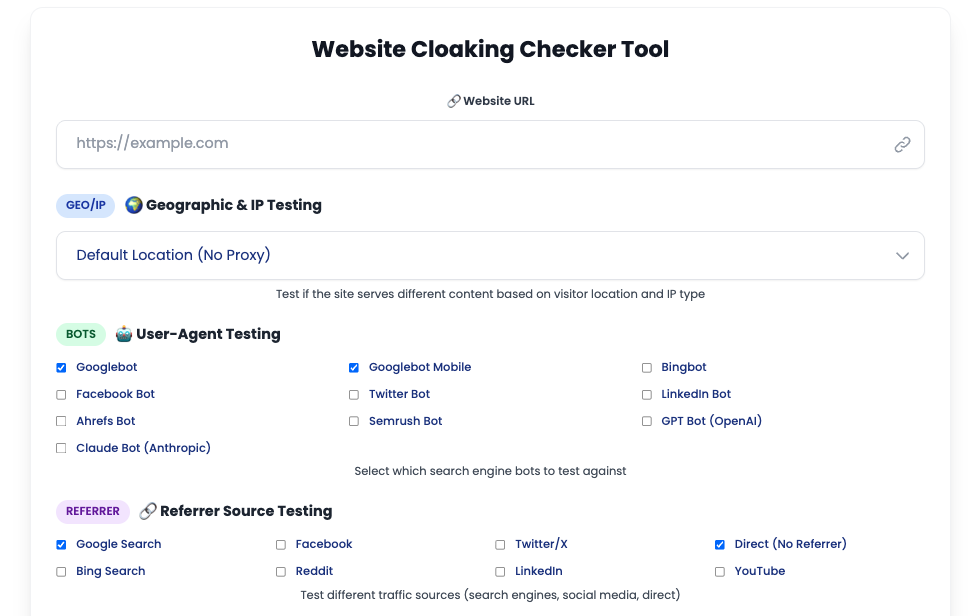
What it tests :
- User-agent cloaking across 10+ bots (Googlebot, Bingbot, GPTBot, ClaudeBot, social bots)
- Geographic cloaking from 40+ countries
- Referrer cloaking from major traffic sources (Google, Facebook, Twitter, Reddit, direct)
- JavaScript rendering differences
- Device detection (mobile vs desktop)
- Cookie-based variations
How to use it :
- Enter the affiliate URL you want to test
- Select the detection methods relevant to your concern
- Choose geographic locations matching your target markets
- Run the check
The tool compares responses across all selected conditions.
A confidence score indicates how likely the page is using cloaking techniques (take that score with a grain of salt !).
Interpreting results : Look for content differences between bot user agents and regular browsers, between different geographic locations, and between referrer sources. Investigate any significant variation.
For monitoring of affiliate pages, combine decloaking checks with continuous affiliate policy monitoring to catch visible violations and cloaked ones.
Building a decloaking workflow
Decloaking shouldn't be a one-time check. Build it into your affiliate compliance process.
When to check for cloaking
New affiliate onboarding : Test landing pages before approving new affiliates.
Fraudsters often start clean, so initial testing establishes what pages look like before any potential cloaking.
Suspicious patterns : Sudden conversion spikes, unusual traffic sources, or complaints from customers about content they saw that doesn't match your records.
Routine audits : Include decloaking in quarterly compliance reviews. Even trusted affiliates can add cloaking later.
After violations : If you've caught an affiliate violating policies, decloak all their other pages. Where there's one violation, there are usually more.
Document and respond
When decloaking reveals violations:
- Capture evidence : Screenshot both the safe page and money page versions with timestamps
- Document the cloaking method : Note which detection method revealed the violation (user agent, geo, referrer, etc.)
- Assess severity : Cloaking itself is a serious violation : it indicates intentional, not accidental, deception.
- Take action : Most affiliate agreements allow immediate termination for fraud.
